The pandemic-related restrictions in 2020 and 2021 led to a surge in all sorts of online activities, from web shopping to Zoom meetings and TV streaming and everything in between. For many older Americans, the last few years have forced a reckoning with technology that had long been ignored or avoided. For the most part, that embrace of web-based products and tools has been positive, opening up opportunities for grandparents and other extended family members to keep in touch, even after the pandemic restrictions began to be lifted. But there is an unfortunate dark side to the recent surge in technology usage by the retiree demographic, taking the form of a substantial surge in elder fraud.
In 2022 alone, the FBI’s Internet Crime Complaint Center received reports of incidents totaling upwards of $3 billion in losses for Americans over the age of 60, representing an 84% year-over-year increase. Affecting nearly 100,000 individuals, the thefts stemming from these scams are by no means minor, with an average loss exceeding $35,000. Internet fraudsters are becoming increasingly bold, savvy, and creative, and the scams are at times impressive in their verisimilitude. We’ll spend some time summarizing some of the most common attacks, while also providing some tips for how to avoid becoming the next victim.
Types of online frauds
While the tactics have gotten increasingly more sophisticated in recent years, the frauds still tend to fall into the same basic categories. The most common types of scams by far remain basic tech and customer support fraud, typically taking the form of “phishing” scams, in which bank, credit card, or other identifying information is targeted. One of the most common current approaches includes “technical support” fraud, in which an attacker professes to be providing fixes for common internet problems, but uses the opportunity to trick victims into allowing remote access to their computers. This remote controlling capability can allow fraudsters to access and obtain a wide variety of identifying personal information, and to disguise their actions in creative ways.
Email-based attacks have also become increasingly aggressive, with the initial messages often appearing to come from entirely legitimate businesses. The most-commonly spoofed companies include a who’s-who of American businesses—Microsoft leads the way as the most frequently impersonated corporation, with Google, PayPal, Yahoo, Facebook, and others also affected. Another notable spate of frauds was recently perpetrated by fraudsters purporting to represent Best Buy’s subsidiary “Geek Squad”. Because so many consumers do legitimate business with these companies on a daily basis, the emails may at first seem legitimate, and many victims believe that they are being contacted in relation to a legitimate account or recent purchase. Attackers will often use the same graphic rendering in their emails that the businesses themselves use, and they will often send their emails from suspiciously similar domain names, perhaps only altering the actual site name by a letter or two.
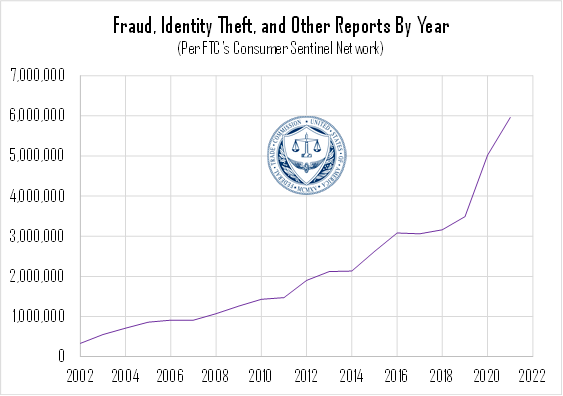
In addition, a surge in cryptocurrency offerings has also introduced a new opportunity for investment-related schemes, and the FBI reports that this is, in fact, the fastest-growing area of elder fraud. These sorts of cases grew by more than 300% in the most recent year of data, taking advantage of widespread public confusion regarding what is (and is not) a “legitimate” crypto product.
The method of the actual attack can vary, but some scammers will ask for bank account (or credit card) information in order to “refund” money that was never actually spent in the first place; once obtained, that account information can be used to steal funds. Other scammers will sometimes process a fake transaction, then request that the victim purchase gift cards or other items in order to help reverse the attacker’s “error”. Some of these attacks can take on seemingly ridiculous premises, but the genesis of the scam almost always seems entirely legitimate.
How to protect yourself
Avoiding these attacks can sometimes be difficult, but many scams start out with notifications or bills for items you didn’t buy, debt collection calls for accounts you did not open, or denials for loan applications that you never submitted. While often concerning, these sorts of messages are very frequently fraudulent. As a general rule, you should only share personally identifiable information (like account numbers, Social Security numbers, and dates of birth) if you initiated the contact with the recipient, via a method known to you to be legitimate. It is also best to avoid sharing this information over email (or especially social media) whenever possible. If you do receive an unsolicited communication that seems legitimate, verify the source using publicly available information. If in doubt, cease the communication and contact the company yourself at a known phone number or email address, perhaps from a recent bill or order confirmation. Be very wary of any communication (or phone call) that expresses extreme urgency or time constraints—very few legitimate businesses require such urgency from their customers, but this urgency (and the panic that it can generate) is one of the fraudster’s most powerful weapons.
When in doubt, a few simple guidelines can help prevent against most financial fraud. First, always double-check the email address that is sending you a message to ensure that it is actually coming from the place it is claiming to come from—if the sending email address does not match the name that appears in your inbox, be suspicious. In addition, never give remote access to your computer desktop to anyone, and cease communicating with anyone who requests it. The same logic goes for anyone who requests that you use gift cards or cryptocurrency in order to solve a problem—these tools are the hallmarks of financial scam artists, and real businesses will always prefer more traditional forms of payment.
Other considerations
Ironically, some measures taken to protect consumers from cyber fraud and other attacks have actually created new opportunities for fraudsters. For example, fraudulent “password reset” emails have recently become a common phishing tool, convincing unwitting victims into disclosing their usernames and passwords to illegitimate recipients. It can therefore be difficult for companies and agencies to protect customers, and in many cases, enhanced personal vigilance will be the only useful tool.
If you suspect that your data may have been compromised, or if you have had an interaction that you’re not sure is legitimate, it will always be important to consistently monitor your credit report, in order to spot anything that seems out of line. The major credit bureaus are each legally required to provide a free credit report each year, and many will provide additional services when data breaches have occurred. At Cypress, we take protecting our clients’ data seriously, and we stand ready to help any who are affected by identity theft, regardless of the source.
